Azure Active Directory: 7 Ultimate Power Tips for 2024
Ever wondered how millions of businesses securely manage user access across cloud apps? The answer lies in Azure Active Directory. It’s not just a directory—it’s the backbone of modern identity management in the cloud era.
What Is Azure Active Directory and Why It Matters

Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service. It enables organizations to securely manage user identities, control access to applications, and enforce security policies across hybrid and cloud environments. Unlike traditional on-premises Active Directory, Azure AD is built for the cloud, offering seamless integration with Microsoft 365, Azure, and thousands of third-party SaaS applications.
Core Functions of Azure Active Directory
Azure AD goes beyond simple user authentication. It provides a comprehensive suite of identity services that empower organizations to manage digital identities at scale.
- User and group management: Create, manage, and organize users and groups across your organization.
- Single Sign-On (SSO): Enable users to access multiple applications with one set of credentials.
- Multifactor Authentication (MFA): Add an extra layer of security by requiring additional verification steps.
These capabilities make Azure Active Directory a critical component for any organization adopting cloud services. Whether you’re using Microsoft 365 or integrating Salesforce, Azure AD ensures secure and efficient access.
Differences Between Azure AD and On-Premises Active Directory
While both systems manage identities, they serve different architectures and use cases. On-premises Active Directory is designed for Windows networks and relies on domain controllers within a local network. Azure AD, however, is cloud-native and protocol-driven, using standards like OAuth, OpenID Connect, and SAML.
- Authentication protocols: Azure AD uses modern protocols like OAuth 2.0; traditional AD uses Kerberos and NTLM.
- Deployment model: Azure AD is cloud-hosted; on-prem AD requires physical servers.
- Scalability: Azure AD scales automatically; on-prem AD requires manual infrastructure scaling.
Understanding these differences is crucial when planning hybrid environments. Many enterprises use both systems together, synchronizing identities via Azure AD Connect. This hybrid approach allows legacy applications to coexist with modern cloud tools.
“Azure Active Directory is not a replacement for on-premises AD—it’s an evolution.” — Microsoft Identity Documentation
Key Features of Azure Active Directory
Azure Active Directory offers a robust set of features that go far beyond basic login functionality. These tools help organizations enhance security, improve user experience, and streamline IT operations.
Single Sign-On (SSO) Across Applications
One of the most impactful features of Azure Active Directory is its ability to provide seamless single sign-on to thousands of cloud applications. Users can log in once and gain access to all authorized apps without re-entering credentials.
- Pre-integrated apps: Over 2,600 SaaS apps like Salesforce, Dropbox, and ServiceNow are pre-configured.
- Custom app integration: You can add any SAML or OIDC-enabled application.
- Password vaulting: For apps without SSO, Azure AD can store and auto-fill credentials.
This reduces password fatigue and improves productivity. According to Microsoft, organizations using SSO see up to a 40% reduction in helpdesk calls related to password resets.
Learn more about app integration: Microsoft Azure AD App Management.
Conditional Access and Risk-Based Policies
Conditional Access is a powerful capability within Azure Active Directory that allows administrators to enforce access controls based on specific conditions. This is where security becomes dynamic and context-aware.
- Device compliance: Require devices to be compliant with Intune policies before granting access.
- Location-based access: Block or allow logins based on IP address or geographic region.
- User risk level: Integrate with Identity Protection to detect risky sign-ins and enforce step-up authentication.
For example, if a user attempts to log in from an unfamiliar country, Azure AD can automatically require MFA or block access entirely. This proactive approach minimizes the risk of compromised accounts.
“Conditional Access turns static permissions into intelligent, real-time decisions.” — Azure Security Best Practices Guide
Multifactor Authentication (MFA) and Identity Protection
Azure Active Directory’s MFA feature adds a critical layer of security by requiring users to verify their identity through multiple methods. Options include phone calls, text messages, authenticator apps, or FIDO2 security keys.
- Available in all editions: Even the free tier of Azure AD includes basic MFA for administrators.
- User registration: Admins can require users to register for MFA during their next sign-in.
- Phishing-resistant methods: Support for FIDO2 keys helps prevent credential theft.
When combined with Azure AD Identity Protection, MFA becomes even more powerful. Identity Protection uses machine learning to detect anomalies such as sign-ins from anonymous IPs or impossible travel (e.g., logging in from New York and London within minutes).
Explore MFA setup: Azure AD MFA Documentation.
Understanding Azure AD Licensing Tiers
Azure Active Directory comes in four main editions: Free, Office 365 apps, Azure AD P1, and Azure AD P2. Each tier unlocks additional features, so choosing the right one depends on your organization’s security and management needs.
Free Edition: What You Get Out of the Box
The Free edition is included with any Microsoft 365 subscription or Azure account. While limited, it provides essential identity services suitable for small businesses or basic use cases.
- User and group management
- Basic SSO to SaaS apps
- Self-service password reset for cloud users
- MFA for administrators (but not for all users)
However, the Free tier lacks advanced security features like Conditional Access, Identity Protection, and device management. It’s a starting point, not a long-term solution for growing organizations.
Azure AD P1 vs P2: Breaking Down the Differences
As organizations scale, they often upgrade to Azure AD P1 or P2. These paid tiers unlock enterprise-grade capabilities.
- Azure AD P1: Includes Conditional Access, hybrid identity synchronization, self-service password reset for all users, and group-based access management.
- Azure AD P2: Adds Identity Protection, Privileged Identity Management (PIM), and advanced risk detection.
For example, P2’s Identity Protection can flag risky sign-ins and automatically trigger remediation workflows. PIM allows just-in-time access for administrators, reducing the attack surface of standing privileges.
Cost-wise, P1 is approximately $6/user/month, while P2 is around $9/user/month. Many enterprises find the investment worthwhile given the enhanced security posture.
Compare licensing: Azure AD Editions Comparison.
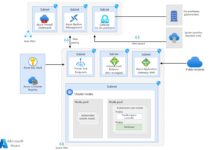
Hybrid Identity with Azure AD Connect
For organizations with existing on-premises infrastructure, hybrid identity is a common and effective strategy. Azure AD Connect bridges the gap between on-premises Active Directory and Azure Active Directory, enabling synchronized identities.
How Azure AD Connect Works
Azure AD Connect is a Windows-based tool that synchronizes user accounts, groups, and passwords from on-premises AD to Azure AD. It supports several synchronization methods:
- Password Hash Synchronization (PHS): Syncs hashed passwords to Azure AD for cloud authentication.
- Pass-Through Authentication (PTA): Validates sign-ins against on-premises AD in real time.
- Federation (AD FS): Uses existing AD FS infrastructure for single sign-on.
PTA is often preferred because it eliminates the need for on-premises federation servers while maintaining strong security. It also supports seamless SSO, allowing users to access cloud apps without entering credentials when on the corporate network.
“Azure AD Connect is the glue that holds hybrid environments together.” — Microsoft Hybrid Identity Guide
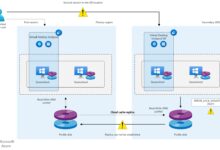
Best Practices for Synchronization and Management
Proper configuration of Azure AD Connect is essential for a stable hybrid environment. Follow these best practices:
- Use filtering to sync only necessary OUs and avoid syncing service or test accounts.
- Enable staging mode on one server to test configuration changes before applying them.
- Monitor synchronization health using the Synchronization Service Manager or Azure AD Connect Health.
- Keep Azure AD Connect updated to the latest version for security and performance improvements.
Additionally, plan for high availability by deploying multiple Azure AD Connect servers in staging mode. This ensures continuity in case of server failure.
Get setup guidance: Azure AD Connect Overview.
Securing Access with Conditional Access Policies
Conditional Access is one of the most powerful tools in Azure Active Directory for enforcing security policies dynamically. It allows admins to define rules that control access based on user, device, location, application, and risk level.
Building Your First Conditional Access Policy
Creating a Conditional Access policy involves defining assignments (who), conditions (when), and access controls (what happens).
azure active directory – Azure active directory menjadi aspek penting yang dibahas di sini.
- Assignments: Select users, groups, or applications the policy applies to.
- Conditions: Set criteria like IP location, device platform, or sign-in risk.
- Access controls: Choose to require MFA, block access, or require compliant devices.
A common first policy is: “Require MFA for all users accessing Microsoft 365 from outside the corporate network.” This balances security with usability.
Always test policies in report-only mode before enforcing them to avoid locking out users.
Advanced Scenarios: Risk-Based and Device Compliance Rules
As your security maturity grows, you can implement more sophisticated policies.
- Risk-based access: Use Azure AD Identity Protection to detect risky sign-ins and require MFA or block access.
- Device compliance: Integrate with Microsoft Intune to ensure only managed and compliant devices can access corporate data.
- Application-specific policies: Apply stricter rules for sensitive apps like financial systems or HR portals.
For example, a policy might state: “If a user’s sign-in risk is medium or high, require MFA and prompt for password reset.” This automated response reduces the window of exposure during potential breaches.
Learn policy creation: Conditional Access Documentation.
Identity Governance and Access Management
As organizations grow, managing who has access to what becomes increasingly complex. Azure Active Directory provides identity governance features to ensure access is granted appropriately and reviewed regularly.
Access Reviews for Periodic Audits
Access reviews allow administrators to periodically verify that users still need access to specific apps or groups. This is critical for compliance and reducing the risk of overprivileged accounts.
- Schedule reviews quarterly or annually.
- Assign reviewers (managers or owners) to approve or remove access.
- Automate removal of unapproved access after the review period.
For example, a project team might be granted temporary access to a SharePoint site. After the project ends, an access review ensures those permissions are revoked.
Entitlement Management and Role-Based Access
Entitlement Management allows users to request access to resources through a self-service portal. Admins can define access packages that bundle apps, groups, and policies.
- Define approval workflows (e.g., manager must approve).
- Set expiration dates for temporary access.
- Integrate with Azure AD roles for fine-grained control.
This reduces administrative overhead and ensures access is granted consistently. It’s especially useful for contractors, interns, or cross-departmental collaboration.
Explore governance: Azure AD Governance Docs.
Common Challenges and How to Solve Them
While Azure Active Directory is powerful, organizations often face challenges during implementation and daily operations. Being aware of these issues helps you plan better and avoid common pitfalls.
Sync Conflicts and Attribute Mismatches
When using Azure AD Connect, attribute mismatches or duplicate proxy addresses can cause synchronization errors.
- Use the IdFix tool to identify and fix directory issues before syncing.
- Avoid using special characters in user attributes that aren’t supported in the cloud.
- Ensure UPN suffixes match between on-prem and cloud environments.
Regularly monitor the synchronization dashboard to catch issues early.
User Adoption and MFA Fatigue
Users may resist MFA due to perceived complexity or “MFA fatigue” from repeated prompts.
- Educate users on why MFA is important for security.
- Use trusted locations or compliant devices to reduce MFA prompts.
- Encourage use of the Microsoft Authenticator app for push notifications, which are faster than SMS.
Improving user experience increases adoption and reduces helpdesk load.
License Management and Cost Optimization
Without proper planning, Azure AD licensing costs can spiral, especially when assigning P1 or P2 licenses unnecessarily.
- Use license assignment groups to manage permissions efficiently.
- Regularly audit license usage and remove licenses from inactive users.
- Leverage free features where possible (e.g., free MFA for admins).
Consider using Azure AD P2 only for high-risk roles like administrators or finance teams.
What is Azure Active Directory?
Azure Active Directory is Microsoft’s cloud-based identity and access management service that enables secure user authentication and authorization across cloud and on-premises applications.
How does Azure AD differ from on-premises Active Directory?
Azure AD is cloud-native and uses modern protocols like OAuth and SAML, while on-premises AD relies on domain controllers and legacy protocols like Kerberos. Azure AD focuses on web-based app access, whereas traditional AD manages Windows network resources.
Is Azure AD free?
Azure AD has a free tier with basic features, but advanced capabilities like Conditional Access and Identity Protection require paid licenses (P1 or P2).
What is Azure AD Connect used for?
Azure AD Connect synchronizes user identities and passwords from on-premises Active Directory to Azure AD, enabling hybrid identity management and single sign-on.
How do I enable MFA in Azure AD?
MFA can be enabled through the Azure portal under “Security” > “Multifactor Authentication.” Admins can require MFA for specific users or enforce it via Conditional Access policies.
Mastering Azure Active Directory is no longer optional—it’s essential for modern businesses. From securing cloud access to enabling seamless collaboration, Azure AD provides the tools to manage identities in a dynamic digital world. By understanding its features, licensing, and best practices, organizations can build a secure, scalable, and user-friendly identity foundation.
azure active directory – Azure active directory menjadi aspek penting yang dibahas di sini.
Recommended for you 👇
Further Reading: